Installation/upgrade with a MySQL database
This guide describes how to install SysAid with Docker using a MySQL database for both new installations and upgrades. For information on SysAid requirements, see SysAid System Requirements.
Before you start:
Please make sure that you have Python 3.5 or above installed.
New Installation
If this is a new installation of SysAid, the first step is to prepare your SQL database.
This involves:
Creating an empty SysAid database with the necessary privileges on your running SQL server.
Configure the database to allow remote login.
Create an empty database on a MySQL server
Run:
mysql -u<user> -p<Password>
create database sysaid;
grant all privileges on <DB name>.* to <DB user name>@'%' identified by '<Password>';Instead of granting all IP addresses, you can grant permissions to the docker subnet - usually “172.17.0.%”, but you need to verify it after docker-ce installation (“docker0” interface in “ifconfig”).
For example:
grant all privileges on sysaid.* to root@'172.17.0.%' identified by '<Password>';
flush privileges; Allow remote login
Example texts included here apply to MySQL servers.
On your MySQL server, edit the relevant configuration file:
Ubuntu / Debian :
/etc/mysql/mysql.conf.d/mysqld.cnfor/etc/mysql/my.cnfCentOs:
/etc/my.cnfIf no “bind-address” line exists, continue to the next step. If there is a “bind-address” line, update it to:
bind-address = 0.0.0.0Verify that the lines below are commented out, if they exist at all.
# skip-networking# skip-external-lockingIf needed, Open iptables rules.
Run
/usr/bin/mysql_secure_installationUpdate your DB details and answer “n” to the question: Disallow root login remotely?
On CentOS-7, add SQL port access to the firewall:
firewall-cmd --zone=public --add-port=3306/tcp --permanent service firewalld restartRestart MySQL server:
Ubuntu or Debian:
/etc/init.d/mysql restartCentOS:
service mysql restart
On your Linux server, install MYSQL client (if not already installed):
Ubuntu:
apt-get install mysql-clientCentOS:
yum install MySQL
Verify you can access SQL DB:
mysql -h<sql server IP>-u<user> -p<Password>Verify you are getting the SQL prompt. If the connection fails, check that the database exists, privileges have been granted, bind-address has been opened, FW open, etc.
Please note:
Do not continue with this procedure unless you can access the SQL server from the Linux Docker unit.
Continue with the General preparations instructions below.
Upgrade
If you are using the MySQL server, make sure that SysAid can connect to the DB. Run:
mysql -u<user> -p<Password>
grant all privileges on <DB name>.* to <DB user name>@'%' identified by '<Password>';
flush privileges;Instead of granting all IP addresses, you can grant permissions to the docker subnet - usually “172.17.0.%”, but you need to verify it after docker-ce installation (“docker0” interface in “ifconfig”). For example:
grant all privileges on sysaid.* to root@'172.17.0.%' identified by 'Password';
flush privileges;Follow the instructions in the General Preparations and Install/Update SysAid Server on Docker sections below.
General preparations
On your Linux machine, copy the following files to the working directory:
docker-compose.ymlpre_requisites.shrequirements.txtSysAid.pyactivation.xml(the account’s activation file)Please note:
The installer files need to be redownloaded with every version upgrade.
If the unit has an external network connection, the script automatically fetches the needed packages.
For faster and clearer output of the preparation script, run it before the upgrade:
Ubuntu / Debian:
apt-get update -y && apt-get upgrade -yCentOS:
yum update -y
Give execution permissions by running in the working directory:
chmod +x pre_requisites.shRun the preparation script. This will install all the required packages:
./pre_requisites.shValidate that the script finished successfully. If the script fails, fix the problem and rerun the script.
Install/update the SysAid server on Docker
If you have a proxy on this server, see Enable Docker pull with proxy, below.
Copy SysAid.py to the server and run it:
python3 SysAid.py installSupply all the requested info:
Command prompt
Description
please confirm running the configuration tool (Y/N):
This step is asking you if you want to configure the installation of SysAid
enter db kind (localhostDB, remoteDB, dockerDB):
Select the DB where your DB is (same computer as SysAid, different computer, inside a docker)
enter db type (mysql):
What type of DB you are using
enter db user [root]:
The DB user SysAid will use to connect to the DB
enter db password:
The password of the selected user on the previous step (the password will not be visible while you type)
please enter DB timezone
Select the time zone where the DB is located (please type as shown on the screen, it is case sensitive)
enter db name [sysaid]:
Select the name of the DB where SysAid will be installed
enter sysaid ip/url [IP]:
Select the IP address SysAid will be reachable (the default value will be the internal IP)
do you want to enable old TLS versions? (Y/N):
Select if you want to use TLS 1.2 or not
please enter max memory for SysAid (units: k/m/g, e.g.: 1048576k/1024m/1g) [2g]:
Select the amount of RAM you want to allocate to SysAid
do you want to copy certificate? (Y/n):
Select if you want to upload an SSL certificate to SysAid
do you want to enable http to https redirection? (Y/N):
Select if you want to redirect your HTTP port to the HTTPS port. Please note that this only redirects to HTTPS port 8443, regardless of whatever custom ports are configured.
please specify a custom http port [8080]:
Select HTTP port. When you configure a custom port, SysAid Docker also listens on the default port (8080). To disable the default port, see the section below.
please specify a custom https port [8443]:
Select the HTTPS port. When you configure a custom port, SysAid Docker also listens on the default port (8443). To disable the default port, see the section below.
Verify installation was successful:
Follow the installation progress by running:
docker logs -f sysaid_sysaid_1When the installation finishes successfully, you should see the line:
******** WELCOME TO SYSAID ! **********
Wait a few minutes and check that the SysAid web page is up at:
http://<IP>:<SysAid port>(IP of the Linux machine with the SysAid docker installation).At the end of this stage, you will have a container running:
docker psCONTAINER ID
IMAGE
COMMAND
CREATED
STATUS
PORTS
NAMES
1b3552a85356
sysaidserver:1.0
"/SysAid/SysAid_co..."
23 minutes ago
Up 23 minutes
0.0.0.0:8080->8080/tcp
sysaid_sysaid_1
SysAid persistency content can be found on the Linux machine under:
/opt/sysaid/data. In this folder, we keep the files that need to be kept after stopping SysAidSysAid can be stopped and started with the following commands:
Stop:
cd/opt/sysaid and run docker compose downStart:
cd/opt/sysaid and run docker compose up -d
Enable Docker pull with proxy (optional)
If your Linux server uses a proxy, you need to enable Docker to pull images through the proxy.
Please note:
These instructions are based on the official Docker documentation, available at Docker Docs.
On Ubuntu:
Create a systemd drop-in directory for the Docker service:
mkdir /etc/systemd/system/docker.service.dConfigure the proxy:
2.1. For an HTTP proxy, create a file at
/etc/systemd/system/docker.service.d/http-proxy.confwith the following content:[Service] Environment="HTTP_PROXY=http://<proxy_host>:<proxy_port>/"For an HTTPS proxy, create a file at
/etc/systemd/system/docker.service.d/http-proxy.confwith the following content:[Service] Environment="HTTPS_PROXY=http://<proxy_host>:<proxy_port>/"
Apply the changes:
sudo systemctl daemon-reloadVerify the configuration:
sudo systemctl show --property Environment dockerRestart Docker:
sudo systemctl restart docker
Disable default ports (optional)
Even if you configure a custom port, the SysAid Docker container also listens on the default ports. You can disable this behavior by editing the docker-compose.yml file that you extracted before running the installer.
Please note:
If you disable port 8443, HTTP to HTTPS redirection will not work.
To disable the ports:
Before running the installer, open the
docker-compose.ymlfile that you extracted.Remove the lines corresponding to the default ports you want to disable.
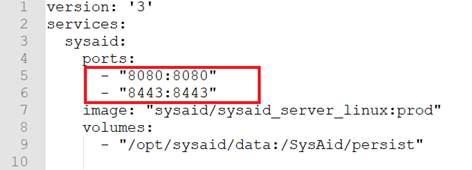
Save the modified file.
Security guidelines and instructions to follow
If you are hosting SysAid via our installed in-house solution, please make sure you follow the security guidelines below:
Make sure you are installing the latest version of SysAid and regularly checking our website for updates.
Ensure that the server running SysAid is updated with the latest operating system versions and security patches.
Access to the server where SysAid is installed should be restricted to your local network or VPN and secured with two-factor authentication (2FA).
Ensure that security controls such as EDR (Endpoint Detection and Response) and WAF (Web Application Firewall) are installed on your SysAid server, just as they should be on any other critical application in your network.
It is strongly recommended to block external access to your SysAid server. If business requirements necessitate external access, make sure to implement protective measures such as a WAF and other security controls. Alternatively, consider using our Cloud SaaS solution, which adheres to the highest industry security standards.