If you store sensitive information in SysAid, you may want to access SysAid using an SSL connection.
It should be noted that certain configurations of SSL acceleration are not supported by SysAid.
There are two options for enabling SSL access to SysAid:
- option 1: SSL Using a Keystore Certificate
- option 2: SSL Using a PKCS #12 Certificate (.pfx file)
If you are using a keystore certificate, you may self-sign your certificate or have an official certification authority sign your certificate.
Option 1: SSL Using a Keystore Certificate
You can use a keystore file as the certificate for enabling SSL access to SysAid. This process involves creating the keystore with all details of the certificate, generating a Certificate Signing Request (CSR), acquiring a signed certificate from a certification authority of your choice, importing the signed certificate back into the keystore file, and applying the certificate keystore to SysAid.
To enable SSL for SysAid using a keystore certificate:
- On the SysAid Server, open a command prompt (Start > Run > cmd).
- Go to the ...\SysAidServer\jre\bin directory.
- Run the following command:
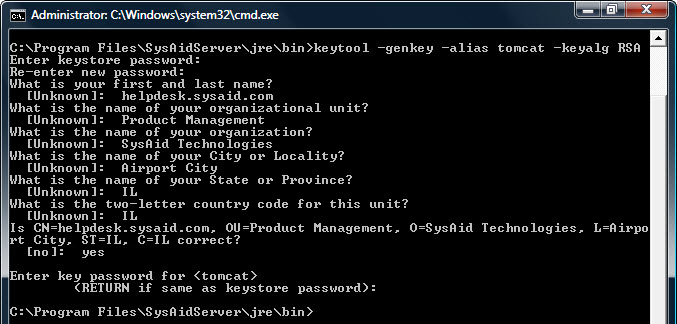
keytool -genkey -alias tomcat -keyalg RSA -keystorename.keystore -validity 365 You may replacenamewith the name of your choice. The validity365 command allows you to change the cert length from the default 90 days to 1 year. This option is only relevant for users with a self-signed certificate. - After the keytool generator has opened:
- Enter your desired keystore password and press Enter.
- Reenter the keystore password.
- For the entry "first name and last name", enter the hostname to be used for accessing the SysAid Server. For example, If you intend to access SysAid via https://helpdesk.yourcompany.com then you need to enter helpdesk.yourcompany.com as your name.
- Line by line, input the remaining information and press Enter , until you get to the confirmation line.
- If the information you entered is correct, type "yes" and press Enter . If you made a mistake, type "no" and press Enter to go back.
- When you are prompted to input a key password for Tomcat, do not type anything and simply press Enter.
There is now aname.keystore file in the directory ...\SysAidServer\jre\bin.Creating a .keystore file
If you would like an official certification authority to sign your keystore certificate, you must complete steps 5 - 12. If you are satisfied with a self-signed certificate, skip to step 13.
- Make a backup copy of the keystore file in case you need to restart the process of importing the certificate for any reason.
- In the command prompt you opened earlier, run the following command:
keytool -certreq -keyalg RSA -alias tomcat -file certreq.csr -keystore name.keystore -keysize 2048 - Enter the password for your keystore and press Enter. There is now a certreq.csr file in the directory ...\SysAidServer\jre\bin.Important!
You must save the keystore file that you use to create the certreq.csr. If you buy a certificate and you don't have the keystore file that you used to generate the CSR, you won't be able to use the certificate!
- Go to the website for the certificate issuer of your choice and follow their instructions for generating your certificate using the certreq.csr file. Save the certificate to ...\SysAidServer\jre\bin.
- Download an intermediate certificate and root certificate (if applicable) from the website of the organization that issued your certificate and save them to the directory ...\SysAidServer\jre\bin.
- Return to the command prompt and import the root certificate into your keystore using the following command:
keytool -import -alias root -keystorename.keystore -trustcacerts -fileroot_certificate_filename
If you were not given a root certificate, skip this step. - Import the intermediate certificate into your keystore using the following command:
keytool -import -alias intermediate -keystorename.keystore -trustcacerts -fileintermediate_certificate_filename - Import your certificate into the keystore using the following command:
keytool -import -alias tomcat -keystorename.keystore -filecertificate_filename
More information about using a certificate signed by an official certification authority can be found on the Apache website at http://tomcat.apache.org/tomcat-7.0-doc/ssl-howto.html - Copy the
name.keystore file to the *...\SysAidServer* directory. - Open the server.xml file located at ...\SysAidServer\tomcat\conf.
- If you are using the a Tomcat version up through 7.0.73, find the following lines:
<!-- <Connector executor="tomcatThreadPool" port="8443" protocol="HTTP/1.1" SSLEnabled="true" maxThreads="150" scheme="https" secure="true" clientAuth="false" sslProtocol="TLS" /> -->Note:If you cannot find this connector, you may be running a different version of Tomcat. Try searching for a connector with the "SSLEnabled" parameter or contact SysAid Support.
Also, if you are running Tomcat version 7 till 9, the displayed protocol is "org.apache.coyote.http11.Http11Protocol". If you are running version 9 or higher, the protocol is "org.apache.coyote.http11.Http11NioProtocol"
- Delete the comment markers at the beginning of the code (<!--) and at the end of the code (-->).
- Immediately after sslProtocol="TLS" and before /> , insert:
keystoreFile="C:\Program Files\SysAidServer\name.keystore" keystorePass="password"Your server.xml should now look like this:
<Connector executor="tomcatThreadPool" port="8443" protocol="HTTP/1.1" SSLEnabled="true" maxThreads="150" scheme="https" secure="true" clientAuth="false" sslProtocol="TLS"" keystoreFile="C:\Program Files\SysAidServer\name.keystore" keystorePass="password" />
- If you are using the Tomcat version 8.5.32 or higher, find the following lines:
<!-- <Connector port="8443" protocol="org.apache.coyote.http11.Http11NioProtocol" maxThreads="150" SSLEnabled="true"> <SSLHostConfig> <Certificate certificateKeystoreFile="conf/localhost-rsa.jks" type="RSA" /> </SSLHostConfig> </Connector> -->Note:If you cannot find this connector, you may be running a different version of Tomcat. Try searching for a connector with the "SSLEnabled" parameter or contact SysAid Support.- Delete the comment markers at the beginning of the code (<!--) and at the end of the code (-->).
- After the SSLEnabled parameter, enter the following text: scheme="https" secure="true"> .
- In the certificateKeystoreFile attribute, replace the attribute value with the path of your keystore file.
keystoreFile="C:\Program Files\SysAidServer\name .keystore" - After the keystore file path, enter the certificateKeystorePassword parameter with your password. certificateKeystorePassword="password "
Your server.xml should now look like this:
<Connector port="8443" protocol="org.apache.coyote.http11.Http11NioProtocol" maxThreads="150" SSLEnabled="true" scheme="https" secure="true"> <SSLHostConfig> <Certificate certificateKeystoreFile="C:\Program Files\SysAidServer\name.keystore" certificateKeystorePassword="password" type="RSA" /> </SSLHostConfig> </Connector>Note : You may change the port from 8443 if you so choose.
- Save server.xml.
- Restart the SysAid Server service.
You have now completed SSL configuration for SysAid. You may now access SysAid using SSL from https://your-server-URL :8443/, as well as from the normal connection you have been using until now.
Option 2: SSL Using a PKCS #12 Certificate
If you already have a PKCS #12 format certificate (.pfx file extension) containing the private key, you can use that in your tomcat configuration instead of using a keystore certificate.
To enable SSL for SysAid using a PKCS #12 certificate:
- Copy the
name.pfx file to the *...\SysAidServer* directory. - Open the server.xml file located at ...\SysAidServer\tomcat\conf.
- If you are using the a Tomcat version up through 7.0.73, find the following lines:
<!-- <Connector executor="tomcatThreadPool" port="8443" protocol="HTTP/1.1" SSLEnabled="true" maxThreads="150" scheme="https" secure="true" clientAuth="false" sslProtocol="TLS" /> -->Note:If you are running Tomcat version 7.0.57 or higher the displayed protocol is "org.apache.coyote.http11.Http11Protocol".
- Delete the comment markers at the beginning of the code (<!--) and at the end of the code (-->).
- After the SSLEnabled parameter, enter the following text: scheme="https" secure="true"> .
- Immediately after sslProtocol="TLS" and before /> , insert:
keystoreFile="C:\Program Files\SysAidServer\name.pfx" keystoreType="PKCS12" keystorePass="password"Your server.xml should now look like this:
<Connector executor="tomcatThreadPool" port="8443" protocol="HTTP/1.1" SSLEnabled="true" maxThreads="150" scheme="https" secure="true"> clientAuth="false" sslProtocol="TLS" keystoreFile="C:\Program Files\SysAidServer\name.pfx" keystoreType="PKCS12" KeystorePass="password" />
- If you are using the Tomcat version 8.5.32 or higher, find the following lines:
<!-- <Connector port="8443" protocol="org.apache.coyote.http11.Http11NioProtocol" maxThreads="150" SSLEnabled="true"> <SSLHostConfig> <Certificate certificateKeystoreFile="conf/localhost-rsa.jks" type="RSA" /> </SSLHostConfig> </Connector> -->- Delete the comment markers at the beginning of the code (<!--) and at the end of the code (-->).
- After the SSLEnabled parameter, enter the following text: scheme="https" secure="true"> .
- Immediately after sslProtocol="TLS" and before /> , insert:
keystoreFile="C:\Program Files\SysAidServer\name.pfx" - After the keystore file path, enter the certificateKeystorePassword parameter with your password. certificateKeystorePassword="
password"
Your server.xmlshould now look like this:
Note : You may change the port from 8443 if you so choose.<Connector port="8443" protocol="org.apache.coyote.http11.Http11NioProtocol" maxThreads="150" SSLEnabled="true" scheme="https" secure="true"> <SSLHostConfig> <Certificate certificateKeystoreFile="C:\Program Files\SysAidServer\name.pfx" certificateKeystorePassword="password" type="RSA" /> </SSLHostConfig> </Connector>
- Save server.xml.
- Restart the SysAid Server service.
You have now completed SSL configuration for SysAid. You may now access SysAid using SSL from https://your-server-URL :8443/, as well as from the normal connection you have been using until now.