Customers integrate SysAid with their LDAP servers for two main purposes:
- Importing their users to SysAid
- Allowing SSO (logging in to SysAid with the LDAP credentials)
SysAid optimizes the process for authentication and authorization of users to ensure that it is always up-to-date and based on access profiles as defined by the customers. To achieve this, our service is SSO capable, using access permissions defined by the customers’ LDAP servers.
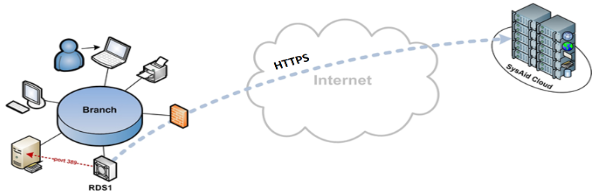
To enable LDAP integration, install our RDS (Remote Discovery Service) in your network, where it can access your LDAP server and manage the communication via standard LDAP ports (389). As the RDS transmits data to the cloud application via the encrypted HTTPS channel, it must be installed on a machine that allows outgoing HTTPS traffic.
When a user logs in to the SysAid cloud application, they enter their LDAP credentials (which are not stored in SysAid) and the RDS verifies the credentials with the LDAP server.
SysAid uses HTTPS and secures the customer data on its cloud servers to ensure that all of the data is protected with no risk of exposure.
Additional points
- The customer can define which LDAP attributes are imported into SysAid.
- The LDAP connector is scoped in our regular penetration testing plan.
- The integration requires a read-only account that should be set up for this purpose. It is a one way connection, that never writes to the LDAP directory. The integration only queries for information, and then updates its internal database accordingly.
- The password that the user enters when logging in, is contained entirely in the HTTPS session. The integration never stores LDAP passwords.
- Optional: We can activate an encrypted LDAP cache option, to speed up the login process and allow login even if the RDS or LDAP server is offline (limited to a defined period). When doing so, we do not store the user password itself - we store a one way encryption of the password and perform the login check against it.
- Optional: If you want to activate our password management module, we require that the SysAid LDAP account have both read and write permissions.