SysAid’s Microsoft Entra ID (Azure) integration allows you to more efficiently manage the users in your company from one central location, by automatically pulling user data from Azure to SysAid. The integration runs these data imports about every 24 hours, saving time and preventing human error that could occur from manually copying the data. This integration can be configured for multiple Azure tenants.
While this imports user information from Azure within SysAid, the users themselves cannot access SysAid unless you also enable the Office 365 Single Sign On integration.
Important:
If you have users that were imported via LDAP integration, to avoid duplicate users and problems with authentication, make sure that:
The users have the same email addresses in the Azure and LDAP repositories
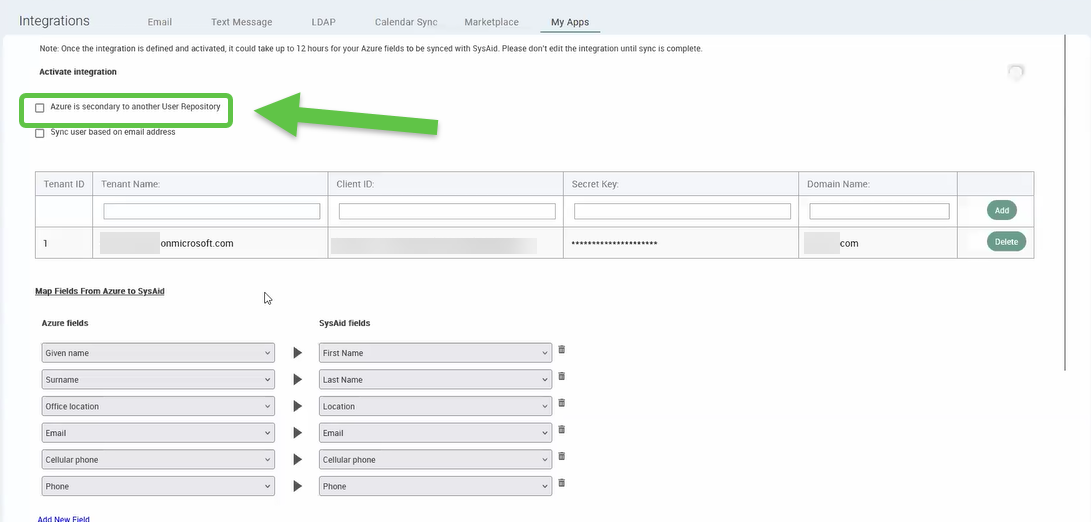
The Sync user based on email address check box is selected in the Azure integration settings
To run these two integrations simultaneously, see Set Up Azure as a Secondary User Repository below.
Connecting Azure and SysAid
First, you’ll need to add the Azure addon to your SysAid account:
In SysAid, go to Connect and click Explore in the Marketplace banner.
Search for Azure and click on the card.
Click Setup and manage. You will be redirected to the My add-ons page, where you’ll see Azure.
Click the gear icon.
Now, you can go ahead and connect the apps - keep your SysAid account in one tab and open a new tab to connect to your Azure portal.
To connect Azure and SysAid, you’ll need:
A Tenant Name
A Client ID
A Secret Key
A Domain Name
Let’s walk you through where to find the relevant details in Azure.
Tenant Name:
In the Azure portal, under Azure services, choose Microsoft Entra ID.
In the Overview section, go to Manage > Custom domain names.
Copy the name with an “Available” status and paste it into the Tenant Name field in SysAid.
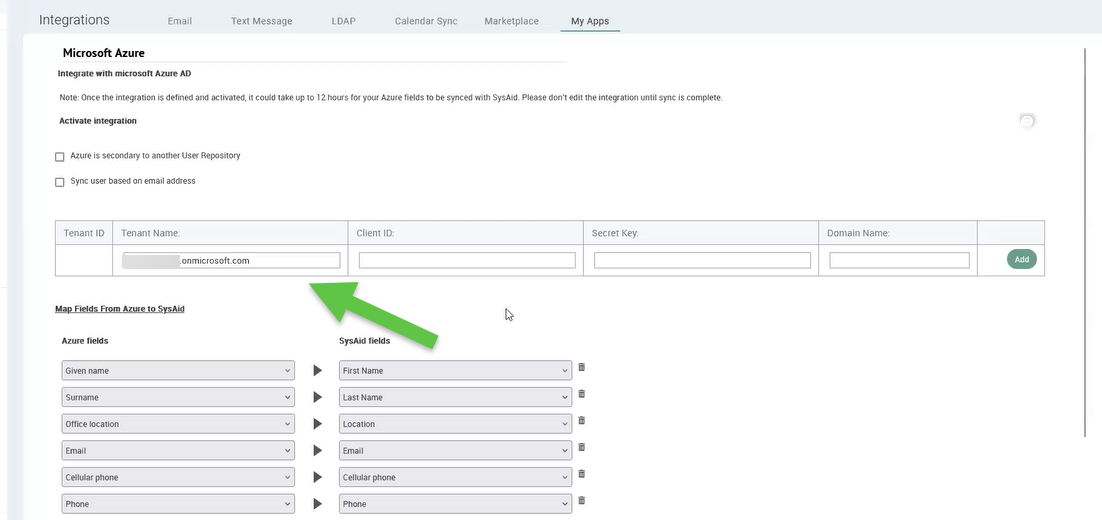
Client ID:
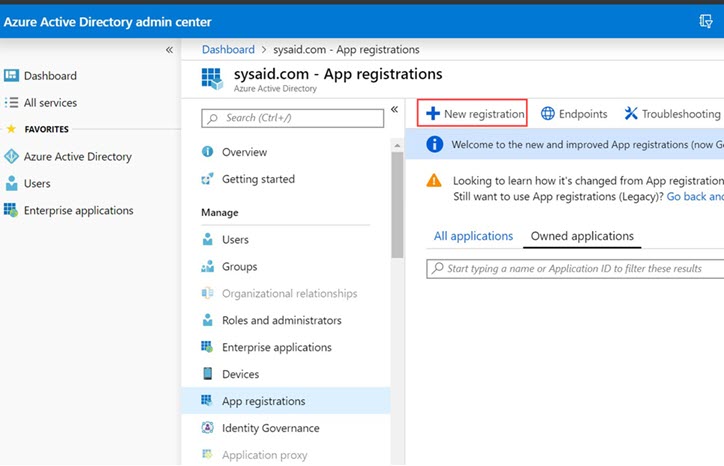
Back in Azure, navigate to Azure Active Directory > App Registrations.
Click New Registration.
In the Name field, enter a name for the application, for example, "SysAid Login".
Click Register.
Back in the app overview screen, click Add a Redirect URI.
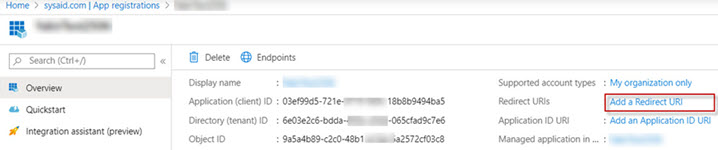
Click +Add a Platform.
Click Web.
In the Redirect URL column, add your SysAid account URI.
Tip:
Your SysAid URI is the URl that you see when logging into your SysAid account. It should be in the following format:
https://www.[YourSysAidURI]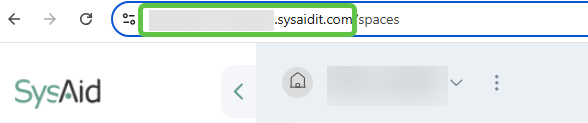

Click Configure.
Click Save.
Click Overview in the menu to the left.
Copy the Application (client) ID for the new SysAid app.
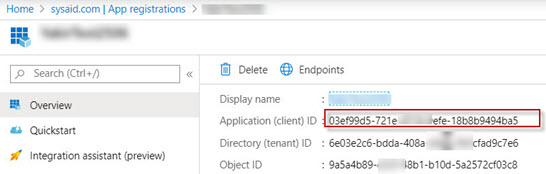
Back in SysAid, paste the copied text into the Client ID field.
Set Microsoft Graph permissions in Azure:
In Azure, navigate to Overview > View API permissions.
Click Add Permissions.
Click Select an API.
Select Microsoft Graph.
Select the following permissions from the Application Permissions section:
Group.Read.All
TeamMember.Read.All
User.Export.All
User.Read.All
Select the following permissions from the Delegated Permissions section:
Group.Read.All
GroupMember.Read.All
User.Export.All
User.Read
User.Read.All
User.ReadBasic.All
Click Save.
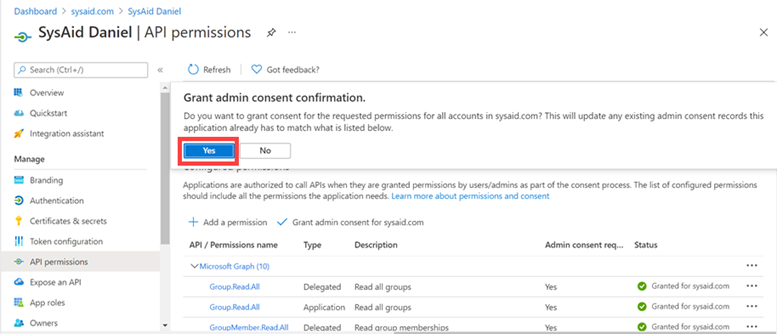
In the Required Permissions section, click Grant permissions.
When prompted, click Yes.
Secret key:
In Azure, under the new SysAid app, go to Manage > Certificates & Secrets.
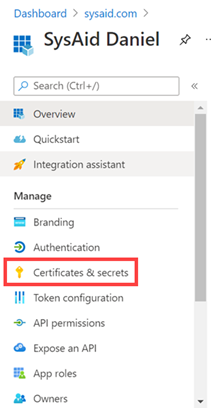
Click +New client secret.
Enter a key name in the description field.
Select the expiration date that suits your security needs.
Click Add.
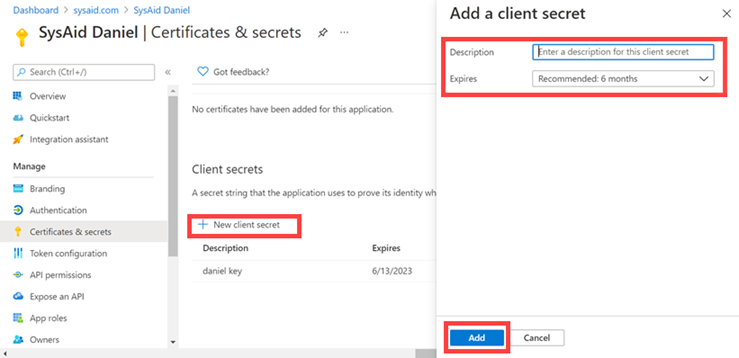
Copy the contents of the key's Value column.
Back in SysAid, paste the copied text into the Secret Key field.
Domain Name:
In SysAid, enter the domain you want, for example - [Your company name].com.
Click Add.
Contact our Customer Care team to ensure proper handling
If you are running SysAid version 20.1.14, enter the following default field mapping text in the JSON field to map.
{"fieldsMapping": [{"sysAidName":"UserName" ,"azureName":"userPrincipalName", "type":"text"}, {"sysAidName":"FirstName" ,"azureName":"givenName", "type":"text"}, {"sysAidName":"LastName" ,"azureName":"surname", "type":"text"}, {"sysAidName":"Location" ,"azureName":"officeLocation", "type":"list"}, {"sysAidName":"Email" ,"azureName":"mail", "type":"text"}, {"sysAidName":"Department" ,"azureName":"department", "type":"list"}, {"sysAidName":"Company" ,"azureName":"companyName", "type":"list"}]}Feel free to make any changes you like. If you are running SysAid Cloud or a later On-Premise version, see the next section for instructions on mapping fields.
Click Save Changes.
Click the slider to activate the integration.
It could take up to 12 hours for your Azure fields to be synced with SysAid. Don't edit the integration until the sync is complete.
Having issues with the setup?
Reach out to our support team.
Set up Azure as a Secondary User Repository
If you are using another user depository (such as LDAP) with SysAid, you can select to set up Azure as a secondary user repository within SysAid. This allows you to take advantage of the SysAid features that require Azure integration while still using the user repository that you are most comfortable with.
To set up Azure as your secondary SysAid user repository:
Select the Azure is secondary to another User Repository checkbox.
Click Save Changes.